Can You Avoid and Defeat Censorship on the Internet?
Can Internet Censorship be Avoided and Beaten?
In our contemporary society, we often boast about living in the most exceptional, the most liberated, and the most democratic civilization that has ever been established. However…upon closer examination, one cannot help but notice the glaring contradictions that rest at the very heart of our world. Despite our ruling junta’s endless claims about our supposedly unparalleled freedom, the prevalence of censorship, de-platforming, and social shaming has reached unprecedented levels. Our current Zionist-Occupied Government and our current Zionist-engineered social order employ tactics that would make Stalin blush.
(image courtesy of knowyourmeme.com)
I recall a time when Google made a contentious decision on YouTube that prompted many creators and viewers, including myself, to set up new accounts and engage in lighthearted acts of rebellion by flooding the comment sections with ASCII art tanks. Nevertheless, in our present era, countless accounts are being banned every day for the slightest deviation away from Zionist-sanctioned and Kosher meta-narratives.
Those who find themselves barred from mainstream social media platforms soon discover that establishing new accounts has become increasingly difficult. If a content creator on YouTube or another major social media network wishes to get his or her account reinstated after transgressing against the Kosher world order, then a daunting process of repentance is demanded. These processes of repentance that are demanded if one wishes to get back into the good graces of YouTube’s Kosher masters are basically humiliation rituals that are designed to demoralize and “Buck-break” whoever displeases a given social media network’s overwhelmingly Jewish censorship committee.

Image courtesy of amazon.com
Yes, “Buck Breaking” serves as one analogy for the degrading process of begging and carrying out insincere acts of repentance in hopes of having a social media network account restored, but this process can also be aptly compared to Communist China’s old “Struggle Sessions” of the 1960s “Cultural Revolution.” One might decide to jump through the Kosher hoops and sacrifice their dignity in hopes of getting their account reinstated, even then, there is still absolutely no assurance of ever regaining access to one’s account.

Image of 1968 Communist Chinese “Struggle Session” furnished courtesy of Newyorker.com
Part One: All Paths Lead to Rome
The uninitiated observer might notice all the censorship that takes place on large mainstream social media networks; however, such people typically fail to grasp how this vile censorship agenda serves the globalist schemes that are designed to lock-down control of whatever information the general public passively receives or can actively access. Why, after all, do seemingly harmless movements such as Flat Earth Theories or UFO discussions face such systematic suppression?
(((Those))) who are heavily invested in the present social order understand that even marginal and seemingly harmless ideologies, such as Flat Earthers and Ufologists, when they are left unchecked, can undermine the legitimacy and power of present ruling narratives. Our readers who have studied these patterns will recognize that multiple pathways of inquiry ultimately lead to questioning the fundamental principles that our current system depends upon for its continued dominance. Our ruling Jewish masters understand that whenever people questions established truths, then this quest for truth and knowledge inevitably leads to National Socialism.
I could elaborate on my own ideological transformation toward National Socialist consciousness, but I prefer to illustrate this principle through two significant examples.
(image courtesy of historyreviewed.best)
My first case study concerns the great George Lincoln Rockwell. After the conclusion of World War II, Naval Commander George Lincoln Rockwell recognizing that his initial struggles targeted the wrong enemy, so in response, Rockwell aligned himself within a National Socialist ideological framework. Before World War II had drawn to a close, General George S. Patton come to the same conclusion that Commander Rockwell had reached after the war’s conclusion, except General Patton was assassinated by Jews before the war’s conclusion.
In the years following World War II, Rockwell began mentoring those within the counterculture movement, and Rockwell’s outreach efforts even inspired some hippies to recognize how their interests aligned with dismantling the existing status quo. The people who were knee-deep in the American Counterculture scene during the 1950s and 1960s that Rockwell reached out to were initially operating outside the system for their own reasons; however, these same people eventually came to understand that National Socialist ideology correctly represented an existential threat to the very power structures which they were instinctively rebelling against.
The second pathway to becoming a National Socialist will be familiar to our regular readers: this path is the Libertarian-to-National-Socialist pipeline. Many Libertarians and Anarcho-capitalists find themselves naturally drawn toward National Socialism ideology over time, which is a phenomenon that we have previously examined thoroughly in this article. Critics often argue that Libertarianism’s fundamental weakness lies in its intellectual demands. While Libertarianism is “sound in theory,” this ideology requires a level of critical thinking that most people simply are not prepared to sustain. Most people are also note even capable of grasping the tenets of Libertarian ideology in the first place.
Besides being a Libertarian, numerous other ideological pipelines to National Socialism also exist. Some of these less common pathways into National Socialism include environmental enthusiasm and advocating for animal rights. After all, National Socialist Germany was the first country in the world to enact modern animal rights protection. Various fitness coaches, after witnessing the deliberate proliferation of processed foods and their disastrous health consequences which such garbage inflicts upon the masses, often develop similar National Socialist leanings.

Many people fail to grasp that those who are now in power understand the trajectory where people unknowingly find themselves drawn to national Socialist ideology as time passes. The ruling Jewish elite can look into the future, and they recognize that once individuals begin questioning dominant narratives, then these same people inevitably progress toward National Socialism.
Historical evidence supports patterns where people question one axiomatic cultural assumption, then soon progress into villages kicking out their local bankers. When villages begin removing local bankers, then such events soon cascade into “Domino Effects” where entire countries and civilizations begin to prioritize their collective well-being over that of individual and greedy accumulation. These cascading events of folkish empowerment may begin when villages start removing their local bankers, but such events soon lead to advanced European nations entirely removing parasitic Jewish bankers.
The cascading “Ripple Effect” where people progress from exploring fringe topics to becoming full-blown National Socialist explains the intensity of current institutional responses to even seemingly benign challenges to orthodox thinking. Jews understand that any crack in their ideological foundation leads to the common people fundamentally questioning the entire structure of Jewish-dominated societies. When people begin questioning one cardinal axiom of their society, then they begin asking more inconvenient questions, hence the aggressive suppression, censorship, deplatforming, debanking, cancel culture, of any alternative perspectives, regardless of how moderate these lines of inquiry might initially appear.

Image courtesy of jewbellish.com
Part Two: Countermeasures
Fighting against powerful opponents is really a fairly daunting experience since anyone who truly challenges an established social order constantly gets beaten down both legally and physically, plus such dissidents get deplatformed and debanked left and right. In light of how difficult resisting a corrupt system can be, it is tempting to feel completely demoralized and powerless in the face of such adversity. Unlike what many people might think, no fight is ever actually easy, yet all enemies have their own unique weaknesses that can be exploited. Even the Great One had to rely on the SA, which was effectively a private security group just so that he could talk to his own people. No such simple freedoms would have ever existed for him without that leveraging that mercenary protection.
Many studies have consistently shown that propaganda needs to be kept constantly above a certain threshold if it is to achieve its aims. Knowing this, one should appreciate the enormous difference between the massive budgets of multi-million-dollar (((Hollywood))) productions compared to the short 15-second videos that a fitness coach or blue-collar worker might post on TikTok.
Living in a Jewish-created bubble is really a fairly common experience since most people have been surrounded by billions of dollars’ worth of Jewish propaganda for their entire lives, yet someone can discover ONE video made that was made by ONE nerd in his basement, then suddenly become aware of the Great One’s greatness. This amazing low-budget and homemade content from the internet often breaks a person’s Jewish-induced spells by presenting unfiltered historical footage and by offering Hitler’s actual words in context as opposed to wrongfully depicting Hitler as some type of Hollywood cartoon villain.

(image courtesy of thepiratebay.org)
The propaganda industry is really a fairly powerful force because it has massive legal resources and massive corporate backing; none the less, when the Hollywood movie industry went after “The Pirate Bay” website things did not work out as they would have liked. The Pirate Bay is a movie-sharing website that is located in Sweden. Despite relentless legal attacks from Jewish-controlled movie-producing conglomerates, these powerful interest groups still could not achieve much success actually shutting down The Pirate Bay website. “The Pirate Bay“ proved to be much more resilient and much more resistant to corporate pressure than the Jews had expected, plus the people behind Pirate Bay were much more committed to their cause than Hollywood’s typical defendants.
In light of this unique situation, The Pirate Bay’s operators can be considered National Socialists because they successfully fought against the predatory practices of the well-funded and well-connected Jewish media and entertainment industrial complex. This connection between The Pirate Bay and National Socialism might seem a bit far-fetched until you realize that Carl Lundström, who is one of the main donors for the infrastructure and legal defense of “The Pirate Bay,” was member of the far right Swedish party named Bevara Sverige Svenskt. Mr. Lundstrom has sadly passed away recently in a (((mysterious))) plane crash (How convenient for that fellow to die when he did and how he did.).

Image of Carl Lundstrom furnished courtesy of wikipedia.org
Executing censorship is really a fairly complex challenge because censoring different types of communication requires different approaches, yet it is always useful to analyze what kind of conversation you are actually trying to have before choosing your communication strategy.
The first types of digital communications in question are the one-to-one discussions or one-to-few discussions which take place within online chat groups. These kinds of conversations should usually be private, and these discussions should also be properly secured, just like having a casual discussion at a pub would be. The second type of communication is the one-to-many format which by definition requires a person to formulate a message, then look for ways to share this message with the world.
One-to-one communication:
These discussions may seem small and insignificant in the scheme of things; however, these gatherings are really a fairly critical battleground; thus, these pocket-sized pow-wows have been under attack for several years now. It is also interesting to note that people are fighting similar struggles that are decades apart often face similar challenges.
Modern communication is much more vulnerable to surveillance than many activists realize, so the consequences are devastating when such systems get compromised. Our German brothers who were fighting during World War II, had their Enigma encryption system broken by adversaries which enabled their enemies to see the Third Reich’s private communications with predictably devastating results. National Socialists today face similar challenges whenever they communicate on any mainstream social media platform and use of the Telegram network persists despite this medium of communication lacking proper encryption and security protocols. Keeping tight security measures is made harder by our natural European values of honesty, openness and integrity; after all, why would anyone “hide” something if they are not doing anything criminal?
(image courtesy of play.google.com)
In reality, today’s threshold for facing severe consequences such as raids and lengthy imprisonment is startlingly low. Imagine this: you could simply be a father who is expressing concerns in a private Facebook chat about refugees “culturally enriching” his child, then this man suddenly finds himself subjected to automatic censorship, or worse. In this case the unfortunate father in question could easily see his residence raided by paramilitary forces, then find himself incarcerated and facing decades behind bars.
And remember, this forceful home invasion and unlawful arrest all happened because this imagined man’s choice of communication medium lacked proper security measures. The implications for having your privacy breeched are vast, and the implications for this trend reach far beyond just the worries of naughty National Socialist sympathizers. In today’s Jewish-controlled societies, even voicing the most mundane expressions of concern about current political, economic, and social trends can lead to draconian repercussions.
When it comes to sending one-to-one online messages, it is absolutely critical to use applications that are designed to minimize metadata footprints while also employing STRONG encryption. Applications such as Signal or SimpleX are highly recommended. ALWAYS, and I mean ALWAYS, set your messages to self-destruct after just a few days or weeks. Why? Because if the information that you are sending to someone else is truly important, then this information should be saved somewhere besides your personal computer or smartphone.
Image courtesy of instructables.com
Potentially controversial Information should always be stored somewhere besides your smartphone of your personal computer because if these devices should ever fall into the wrong hands, then the bad actors would be able to retrieve whatever information is stored on your personal devices. Storing information outside of your personal devices is crucial, so you should always keep a very limited window of recent activity stored, always just store a few days’ worth of logs at worst.
But here is another thing to keep in mind: Signal, for instance, REQUIRES a phone number to activate, and that number can often be traced back to you, so while encrypted messengers are indispensable tools, they should not just be reserved for discussing sensitive or controversial topics.
No, these encrypted applications such as Signal should be your go-to for any conversations that you have, even casual chats with friends or family. Why? Because if you ONLY use them for important or controversial discussions, it can raise red flags, making it easier for you to become a target. Remember that our (((adversaries))) are skilled at frequently changing their names, and you can adopt similar strategies.
Remember, you do not have to use your real name or your real telephone number when creating accounts on some messaging applications, so use a pseudonym or any nickname that you prefer, and also consider using a burner sim card that you bought with cash which is not tied to your identity for your Signal account.

Image courtesy of shutterstock.com
It must be noted that telephonic communications and SMS services should be strictly avoided, because these channels are readily intercepted and, in numerous instances, communications through these channels are subjected to systematic automated recording.
One-to-many communication:
Now, let us tackle a challenge which is inherently more difficult because it demands that we broadcast our message to the widest possible audience while reaching as many people as we are able. However, here is the catch: if a message is encrypted or overly obscure, then it is at risk for failing to connect with a broad audience.
Crucially, the balance between security and accessibility must be carefully balanced. Often, members of the “NS” community take an approach where they upload their content to numerous platforms like YouTube, Odysee, and Rumble; however, while this strategy may seem effective at first, it fundamentally overlooks a critical issue. So, what is the critical issue? The issue is: whatever data is posted on these networks remains under the control of large cloud services providers who are known to collaborate with Jews and other Synergists to enforce bans across multiple platforms. These underhanded bans by cloud information storage providers can result in the outright destruction of entire channels, and consequently, the loss of valuable content.
(image courtesy of youtube.com/@ZoomerHistorian, The modern NS experience on YouTube, watching (((Marvel – Disney indoctrination))) before accessing a documentary)
Moreover, if National Socialist digital content providers publish their content across multiple social media networks, then such practices neglect to empower their content’s viewers themselves. If audiences continue to rely on these major Jewish and Synergist social media providers, then audiences remain tethered to systems that will betray their trust whenever opportunities arise. Thus, while spreading good National Socialist content far and wide is a crucial activity, it is equally vital to ensure that the methods which are used to disseminate good content do not perpetuate dependence on hostile entities.
Platforms like YouTube are increasingly requiring their users to be logged-in, and creating these “log in” accounts on many social media networks often demands that potential users disclosure their personal identities. Disclosing personal identities to gain viewing accounts on social media platforms potentially exposes individuals to the risks of having their personal communications get hacked or these people might potentially find themselves being targeted legally or physically. Additionally, this requirement to provide personal data to view content that is posted on a social media platform subjects a National Socialist’s content viewers to (((relentless))) and (((intrusive advertisements))).
Take, for instance, archive.org, which is a rather well-known internet content-archiving project. Copious “National Socialist” content is hosted on this platform, including entire documentaries, articles, PDF files, and complete books. Should archive.org ever go down for any reason; be it a hack, an ideological takeover, or some other type of unforeseen circumstances, then this loss would be tremendous. The owners of archive.org have explicitly gone against the “Evil Nazis” and have voiced their dislike for “Evil Nazi” content within their website on countless occasions.
It is completely understandable for people to rely on third-party services for hosting their online content; after all, large-scale data-archiving is no simple feat. Storing, organizing, and retrieving massive amounts of data demands substantial resources such as powerful computers, ample storage solutions like hard drives, plus high-speed connectivity options like fiber-optic connections. The sheer scale of managing all this data can be overwhelming for anyone who is effectively a dissident and now finds himself locked out of using any mainstream services and their many resources.

Image courtesy of utilitydrive.com
However, here is some the good news! There is a solution available! The solution to unreliable data storage companies draws its inspiration from the likes of The Pirate Bay…enter BitTorrent. So, what is BitTorrent? This system is a remarkable protocol that is designed to facilitate decentralized sharing for computer files.
With BitTorrent, the power lies in the hands of the users, so anyone who possesses a copy of a file can share it with others who may need it. BitTorrent’s file sharing service creates a network where content distribution becomes a collective (socialist) effort rather than relying on a central server. BitTorrent’s decentralized approach to sharing files and data across the internet not only reduces dependency on third-party hosting services, but it also ensures that content remains accessible even if one source goes offline. BitTorrent represents a brilliant way to democratize access to information because it ensures that data is never lost due to hardware failures or censorship.
So, how does one create and use BitTorrent?
First, let us posit a necessary disclaimer: utilizing Torrent technology invariably exposes one’s IP address. Should this prove concerning, then employing a VPN is strongly recommended. With this preliminary matter properly addressed, we may proceed to the practical aspects of using Torrent Technology. One requires a Torrent client for both creating and downloading existing Torrents. Among the numerous clients that are available, qBittorrent (https://www.qbittorrent.org/) has proven itself to be a reliable option which is freely accessible to users.
The following explanation will detail the process of downloading Torrents, presuming one’s preferred content creator has already established a torrent archive.
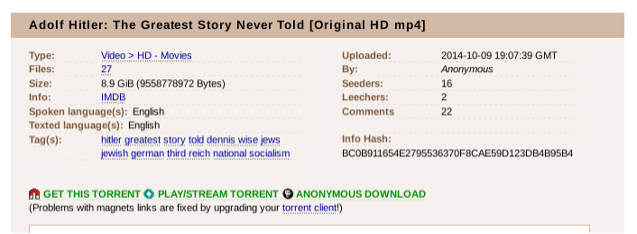
(image courtesy of thepiratebay.org)
For this demonstration, the film “The Greatest Story Never Told,” which is freely distributed through Torrent networks, shall serve as our example. Utilizing “The Pirate Bay” platform, one may readily locate the desired Torrent by using a common search engine function. When using The Pirate Bay’s in-house search engine, particular attention must be paid to two metrics: the quantity of the “Seeders” and “Leechers” that are present.
Elevated numbers in these categories often indicate superior torrent quality, whether in terms of resolution (HD versus SD) or in terms of authenticity. Paying attention to the Seeders and Leechers within a Torrent is necessary because adversaries routinely distribute counterfeit torrents or malicious software through this vector.
In light of the dangers that are endemic to loading Torrents, one must always identify either the magnet link or the Torrent file. These two formats are fundamentally identical because both consist of instructions that enable qBittorrent to retrieve and reconstruct the original content by using distributed downloading from fellow users. Upon selecting either the magnet link or the Torrent file, your Torrent client will commence the downloading process automatically.
Establishing torrent archives must be regarded as a paramount priority for National Socialist content creators. While continued utilization of major technology platforms remains advisable, one must not place exclusive reliance upon these entities for content preservation and for broadcasting. The meager revenues that are derived from advertising on social media networks and on in-house personal websites represent an unstable income source that is still entirely subject to the capricious demands of advertisers who commodify one’s audience. These dominant social media platforms deliberately obstruct content’s downloading capabilities because they fear independent distribution and they wish to maintain their (((monopolistic control))).
Creating a Torrent requires neither technical expertise nor powerful computing resources; rather, a Torrent’s efficacy derives from a collective swarm of users. To create your first Torrent, simply navigate to the torrent client’s top menu (qBittorrent in this instance) and select “Tools” → “Torrent Creator” to access the torrent creator tool.
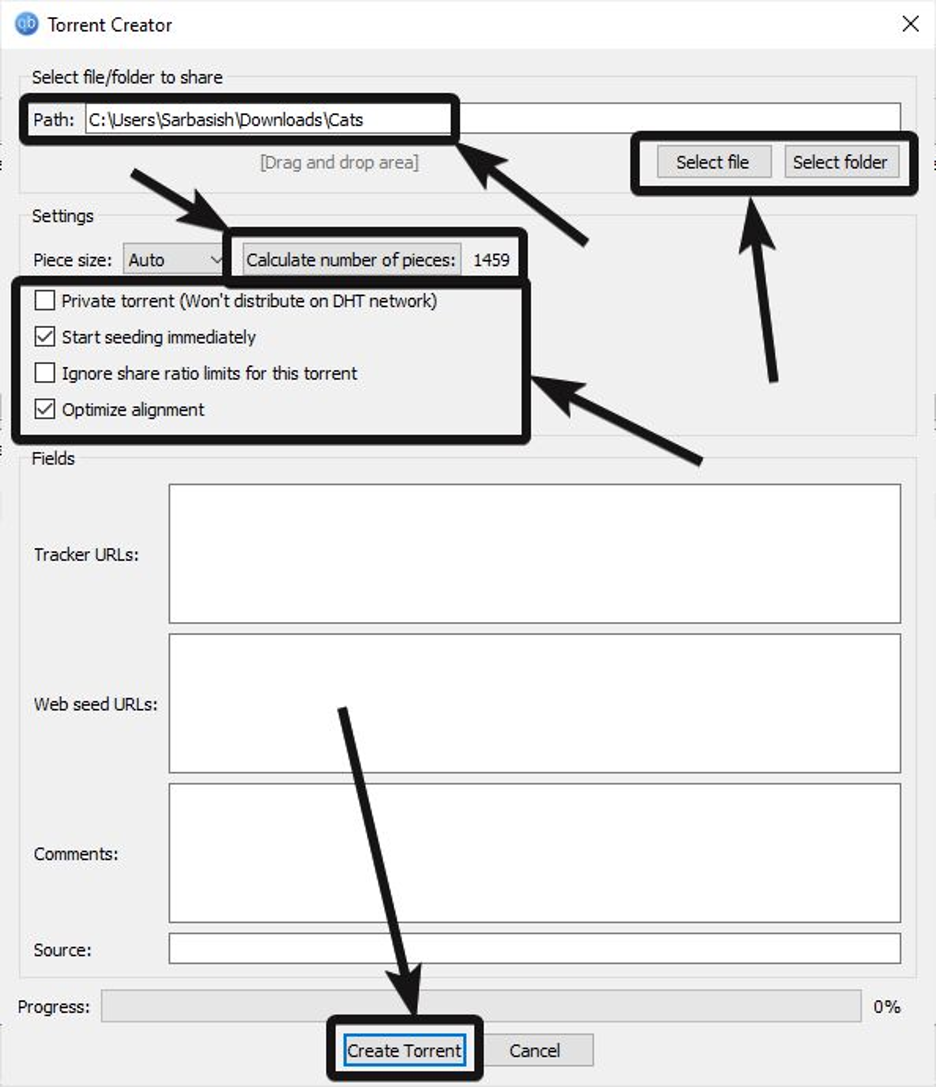
(image courtesy of how2shout.com)
This tool should be clear enough to see, but if you encounter difficulties:
- Path: This term indicates the folder on your computer where your content is stored. It is recommended that you share entire directories rather than many small Torrents because this way of doing things makes discovery easier for users who will never need to find dozens of separate files.
- Settings: This term allows the torrent program to automatically calculate the number of pieces to send, plus it enables both immediate seeding and alignment optimization.
- Tracker URLs: This term describes a needed list of public trackers that help users find and access your Torrent. These lists are readily available online through any search engine by searching “tracker list.”
- Web Seed URL: This option can be ignored for now.
- Comments: These pieces of wording provide a simple description of the Torrent’s contents along with a brief summary.
After configuring these options, simply click “Create Torrent” to complete the process. You may then share the resulting magnet link or torrent file with your audience.
After configuring these settings, click “Create Torrent” to finalize the process. The resulting magnet link or torrent file can then be distributed to your intended audience.
To easily test your torrent-creation abilities, try to download your first torrent from a different computer. While it may be tempting to close your Torrent client, content creators and users should still leave their Torrent client open whenever possible to ensure availability for those who are seeking to download content. It is essential to remember that Torrents become effectively inaccessible whenever no users are actively sharing them.
—
Addendum:
James Rousse:
Hello Ted,
I would also like to note that some pretty reputable people have told me more than once that any digital communications at all are not really safe, so for this reason I do not have much faith in VPNs or “Super Secret” communication applications. I have been told by more than one organization [names redacted] that pretty much all but the most crazy encryption applications are a joke when dealing with the likes of the Mossad and their offshoot organizations such as the NSA, the CIA, and the FBI.
I have also been told that it is better to be just labeled as a garden-variety racist and antisemite than to be labeled as a real troublemaker, so I have been told that it is best not to be too secretive about your online activities. According to more than one reputable source, those who are too secretive are the ones who get their doors kicked in.
Ted:
Regarding encryption and “ultra-secure” applications, I share your perspective to some extent. Criminal organizations frequently fall into the trap of trusting seemingly sophisticated apps that are actually operated by law enforcement (a prime example being Operation Trojan Shield: https://en.wikipedia.org/wiki/Operation_Trojan_Shield).
It’s important to note that Telegram lacks proper encryption, so it’s unsurprising when users face legal consequences due to their communications on the platform. This is precisely why I advocate for mainstream applications like Signal, which are built with everyday users in mind and are designed with robust security features. I’ve been involved in several cases where Signal was used, and no data could be extracted. While I can’t share specifics, you can find similar examples like the Amazon CEO’s use of Signal’s disappearing messages feature to protect sensitive communications. https://www.businessinsider.com/amazon-jeff-bezos-encrypted-messaging-auto-delete-ftc-antitrust-2024-5?op=1
I believe that the narrative which runs something like… “hackers can breach anything anyway, so why bother with security” is actually a form of psychological manipulation that is designed to discourage people from taking protective measures.






